
Ensure Secure Data Transmission without a Secure Channel

Intercepting and reading an email is not hard task even for malefactors-beginners. In order to protect your confidential info from security risks related to
Main problems that may occur upon sending files through email:
-
Unsanctioned interception and modification of emails.
-
Reliability and availability of the service as a whole. Errors, such as typing in an incorrect address or destination mix-ups, can put data sent via email at risk.
-
Data is susceptible to malware.
-
Data can be compromised due to invalid format or user's actions that might compromise security system of email client or server.
-
Legal issues: the need to check the source of a message, etc.
-
Measures required for controlling remote access to email.
-
Form a complex approach towards file transfer security.
-
Check
content of files and messages for errors and malware. -
Block leaks of confidential info in real time.
-
Security policy must comply with the law and industry standards.
-
All transferred files must be revised by the system admin on a regular basis.
General scheme of safe data exchange
Picture 1 schematically demonstrates the way the app works. According to this scheme, files can be sent by both internal and external users (with limitations). Each message is checked for malware and errors, and it also must meet size and quantity limitations. If a sender is an external user, an email must be revised and approved by the admin as well. Each email is signed with a Digital signature. It helps to eliminate the chance of interception. Upon receiving an email each user must be
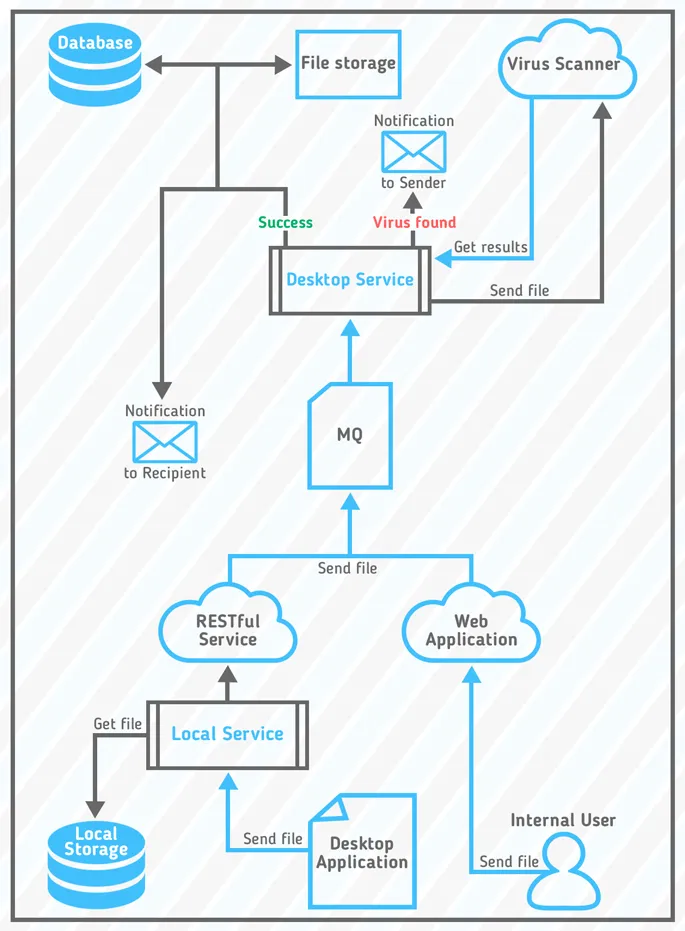
Picture 1 - General scheme of the software complex
Final points
Main criteria for a Security System evaluation:
- Compliance with requirements applied to High Load Systems
- Protection from all sorts of modern threats
- Compliance with the law
- Simple and intuitive User Interface





